
Microsoft Access has been a familiar database tool for many credentialing and certification organizations over the years, thanks to its reputation as a low-cost, simple data management solution. But the truth is, Access wasn’t made for web applications or distributed work—it’s a desktop application. That means it comes with big risks that can jeopardize the security and integrity of your credentialing programs when used collaboratively.
That may seem alarmist, but the reality is that Access databases were never designed to meet the demands of today’s credentialing industry—or offer security against the newest range of cyberthreats.
Here at ROC-P, we’ve heard our share of harrowing stories of missing, corrupted or stolen data from organizations relying on Access databases, and know that the threat is real.
If your organization is still relying on a Microsoft Access database to manage certification data, here are six risks to your data you should know about—and a safer alternative to consider if you’re ready to make the switch.
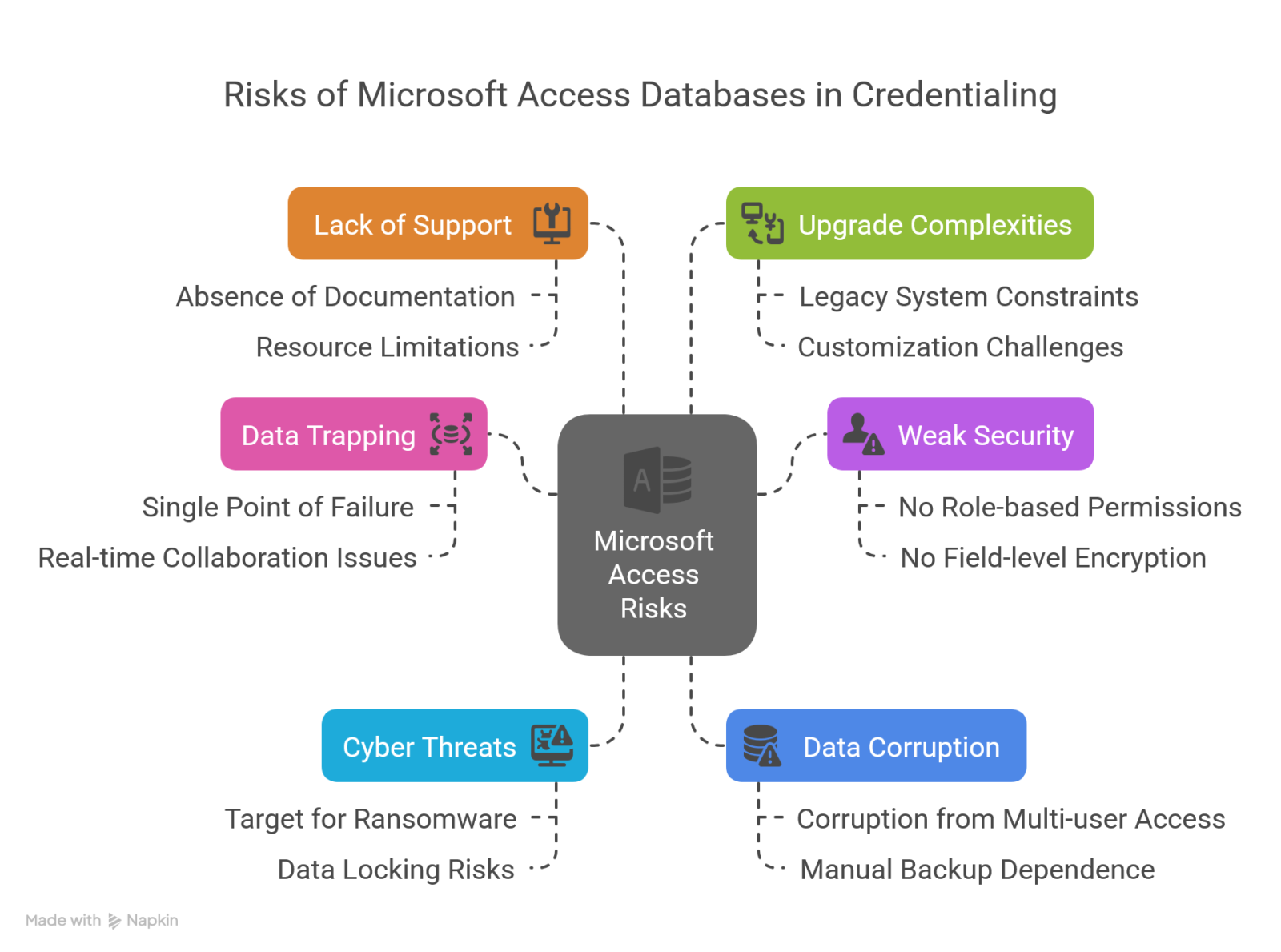
1. With Access, Your Data is Trapped in One Place
At first glance, Microsoft Access can feel deceptively modern—especially for organizations that have been using it for years. After all, if your team is accessing an Access database from a shared drive or remote desktop connection, it can feel like you’re already operating “in the cloud.”
But that sense of flexibility is misleading. Access databases (.accdb or .mdb files) are fundamentally local files, stored on individual devices or an internal server. And while remote access might be technically possible, it comes with all the risks and limitations of a centralized, hardware-dependent system.
The biggest risk? Having a single point of failure. If your device crashes or your server goes down, or if the file is accidentally deleted or corrupted, your data could disappear in an instant.
For modern certification boards managing complex data with remote teams, remote exam proctors, or distributed staff, this limitation is more than an inconvenience—it’s a liability.
2.Weak Security Leaves You Vulnerable
When it comes to managing sensitive certification data, security isn’t optional—it’s essential. And yet, Microsoft Access databases were simply not designed with today’s cybersecurity threats in mind.
Most Access databases rely on little more than basic file-level password protection. But once a user has access to the database, they typically have access to everything. There’s no ability to assign user roles or restrict permissions to sensitive fields. There’s also no field-level encryption, or multi-factor authentication (MFA) to provide an added layer of protection against unauthorized access.
In a world where credentialing organizations handle personal data, exam results, and confidential records, this lack of security controls is a major liability. It exposes your organization to internal risks, accidental data breaches, and external cyber threats.
This isn’t just about keeping bad actors out—it’s about providing confidence that your most valuable data is protected at every level.
3.Ransomware, Cyber Threats Target Older Systems
One of the greatest threats facing credentialing organizations today is ransomware—malicious software that locks users out of their systems or encrypts their data until a ransom is paid. Unfortunately, older systems like Microsoft Access databases are often prime targets for this kind of attack.
Access databases typically lack the modern security defenses needed to withstand today’s sophisticated cyberattacks. When certification data is stored in a local Access file on a single device or server, that file becomes an easy target. If ransomware finds its way onto that device—whether through a phishing email, malware, or network vulnerability—the entire database can be locked and held hostage within moments.
Even if a ransom is paid, there is never any guarantee that your data will be returned safely or in its original state. The loss of access to critical certification records, historical data, or exam results can bring operations to a standstill, impacting not only staff workflows but also certificants, who are trusting your organization with their personal data.
4.Data Corruption is Common, And Costly
While ransomware attacks tend to grab the headlines, not all data loss happens at the hands of bad actors. In fact, one of the most persistent risks facing certification boards using Microsoft Access is the very real threat of data corruption, often caused by ordinary day-to-day use.
Unlike cloud-based systems that are designed for real-time collaboration and automatic data integrity checks, Access databases were never built to accommodate multiple users editing data at the same time. When several staff members attempt to access and update the same Access file, the risk of data corruption skyrockets.
Power outages, unexpected system shutdowns, or simply failing to properly close out of the database can all cause harm to the file. Worse yet, if someone accidentally deletes the Access database file itself—a scenario that’s all too common in shared-drive environments—your entire certification history could disappear in seconds.
These risks are further amplified by Access’s lack of version control. If an error is introduced, there is often no easy way to revert back to a clean, previous version of the database. And with no built-in audit trails or automatic backups, certification boards are left to hope that manual backups exist (and are recent enough to matter).
5.No Support When Things Go Wrong
One of the big challenges with Microsoft Access isn’t just the technology itself—it’s the absence of reliable support when things go wrong.
In many organizations, Access databases were built years ago by staff or consultants with varying degrees of technical expertise. Often, the original creator has moved on, leaving behind a fragile, undocumented system that today’s IT teams are reluctant—or even outright refuse—to touch.
The result? Certification boards are left managing critical processes with little or no technical safety net. Any update, repair, or customization requires resources and/or experts with very specific knowledge of the Access platform.
Even if your Access database is stable today, the question isn’t if you’ll encounter a problem—it’s when. And when that time comes, will you have the expertise and resources necessary to recover quickly?
6.Upgrades Are Risky and Complex
For many certification boards using Microsoft Access, upgrading their database can feel like defusing a bomb. What may seem like a routine update—a new version of Microsoft Office, an operating system upgrade, or a server migration—can have unintended and catastrophic consequences for Access databases.
That’s because Access is a legacy system, tightly bound to very specific versions of its software environment. Even small discrepancies between versions of Access or Office can result in lost functionality, broken forms, or database crashes. For certification staff who are not deeply technical, navigating these issues can be frustrating and time-consuming—often requiring expensive outside help to resolve.
Beyond support challenges, Access databases simply weren’t built to scale. They lack the flexibility and advanced features of more modern database systems, and are difficult to integrate with other applications or technologies. There are no modern APIs for integrating with other tools, no mobile-friendly interfaces for remote users, and a limited ability to customize the user experience to fit evolving needs.
As certification boards grow and evolve—adding new programs, expanding to new regions, or managing larger candidate volumes—Access can struggle to keep up. Is that something your growing program can afford?
What’s a Better Alternative to Microsoft Access?
Ultimately, the real danger of Microsoft Access isn’t its technical and security limitations—it’s the hidden costs that emerge every time your database slows down, breaks, or puts your organization at risk. If your organization is trying to achieve operational excellence, Access is not going to get you there.
Certification boards deserve tools that enable them to thrive, not hold them back.
That’s where ROC-P comes in.
ROC-P is a cloud-based credentialing management system (CMS) designed specifically to meet the needs of today’s credentialing organizations. It offers all the functionality boards need to operate efficiently and securely, without the headaches of legacy systems.
With ROC-P, you will gain:
- Secure, cloud-based access to data from anywhere, on any device
- Role-based user permissions and field-level security controls
- Real-time collaboration without fear of file locking or data overwrites
- Automated backups and built-in disaster recovery protections
- Seamless upgrades and new feature rollouts with no downtime
- Expert onboarding, training, and long-term support from credentialing specialists
Perhaps most importantly, ROC-P was designed to scale alongside your organization. Whether you’re managing a regional certification program or a global credentialing enterprise, ROC-P provides the reliability, flexibility, and security you need to focus on what matters most: advancing your mission and serving certified individuals.
If you’ve outgrown Microsoft Access, or are tired of living with its risks, there’s never been a better time to explore what’s possible with ROC-P. Reach out for your personalized demo today!
